Видео с ютуба Algorithmic Security

Hash algorithm in cyber security | Debug entity

Cryptography and Network Security \ Lecture No. 5 (DES Algorithm)

Blockchain Security - Secure Hashing Algorithm - SHA

Bcrypt vs Argon2 – Which is the Best Password Hashing Algorithm?

Lecture 17 | RC4 Cipher | RSA Algorithm | Cryptography and System Security | Sridhar Iyer

Use approved and secure algorithms for hashing passwords #cybersecurity #programming #development

CS8792 - Cryptography and Network Security | Unit 3 - RSA Algorithm

RSA ALGORITHM || Asymmetric Key cryptography 🗝️Cyber security #bca #cybersecurity #gatecs #ugcnet

EXTENDED EUCLIDEAN ALGORITHM (CRYPTOGRAPHY AND NETWORK SECURITY)

Data Security - RSA Algorithm

Security considerations for blockchain consensus algorithms

#1 How to write Algorithm || Basics of Programming || S.M. Security
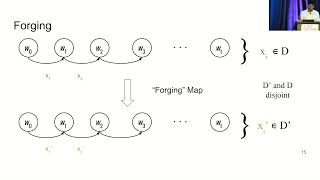
USENIX Security '22 - On the Necessity of Auditable Algorithmic Definitions for Machine Unlearning

Multiplicative Inverse by Extended Euclidean Algorithm || Cryptography || Network Security

El Gamal Algorithm | Cryptography and Network Security

CRYPTOGRAPHY & NETWORK SECURITY Unit-2 AES Algorithm

Алгоритмические культуры и безопасность — презентация Лучианы Паризи — 18–19 июня 2015 г.

Cyber Security|ATM hacking|Neural Cryptography|Digital signature|What,s app|Algorithm|End encryption

Euclidean Algorithm Problems (KTU CSE 409 - Cryptography And Network Security - Module 3)

HVS-3272. Hybrid Encryption Algorithm for the Data Security of ESP32 Based IOT-Enabled Robots